Introduction
Even though many phishing sites have telltale signs that make them relatively easy to identify, a surprising number of individuals still fall prey to their deceptive tactics. Scammers often use a sense of urgency to pressure potential victims into making hasty decisions without taking the time to think things through or verify the legitimacy of the offer
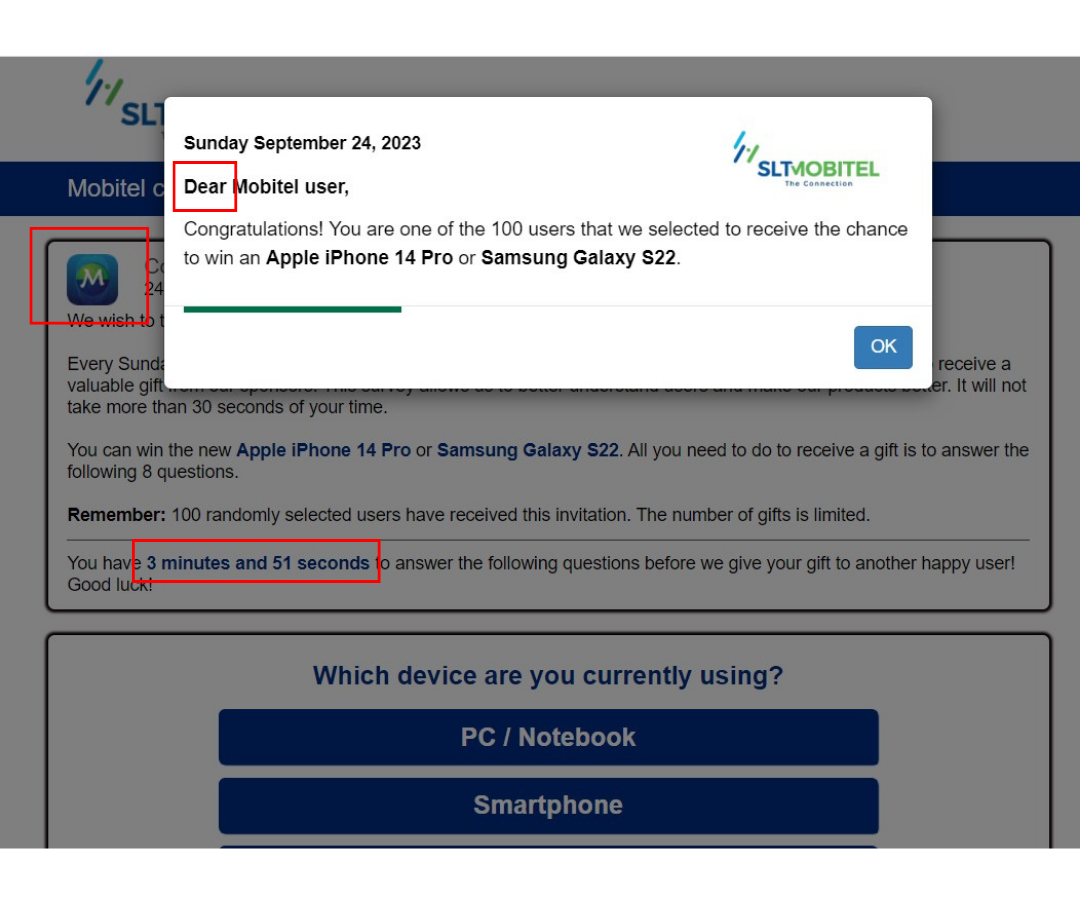
How you can identify a scam prize ?
Phishing is a form of social engineering attack wherein the attacker poses as a reputable source to extract personal or financial information from the target. Typically executed via email, phishing attacks may also occur through social media, text messages, and even phone calls.
- Too Good to Be True: If you receive a notification about a significant prize or award that you don't remember entering or that seems too good to be true, it's a red flag.
- Immediate Action Required: Scammers will often tell you that you need to claim the prize immediately or within a very short timeframe. Phrases like "Act now!" or "Limited time offer!" are commonly used.
- Pressure Tactics: You might be told that if you don't claim the prize immediately, you'll lose the opportunity forever. This tactic is used to prevent you from taking the time to verify the legitimacy of the offer.
- Request for Personal Information: Scammers might ask for personal details, supposedly to verify your identity or process your prize. Legitimate contests or sweepstakes will not ask for sensitive information like Social Security numbers or bank account details over email or phone.
- Payment or Purchase Required: If you're told you need to make a purchase, pay a fee, or provide credit card details to claim your prize, it's likely a scam. Genuine prizes do not require payment to claim.
- Vague Details:Scammers often provide vague or incomplete details about the prize, the organization offering it, or the reason you've won. If you can't find clear information or if the details seem sketchy, be wary.
- Check the Source:Look at the email address, phone number, or website URL. Scammers often use addresses that look similar to legitimate ones but have slight misspellings or extra characters.
Conclusion
If you suspect something might be a scam, take the time to research and verify. Contact the supposed organization directly using contact information from their official website (not from the email or message you received). Remember, legitimate organizations will not pressure you with a false sense of urgency to claim a prize or provide personal information.
